Skypenote Address
Ethan Zuckerman kicked off m4change with a Skypenote address on social changes generated by mobile technology.
Here are the main conclusions I drew from his presentation:
- Ownership versus access to technology: While not everyone in Tanzania owns a mobile phone, 97% have access to one.
- Endogenous versus exogenous protests: Protesters in Jordan turned up in front of the US Embassy not because they intentionally sought to join a centralized political movement but because five of their friends were going. Friend-to-Friend (F2F) communication?
- Impact of ICTs on nondemocratic regimes: Those who doubt that modern ICTs pose a threat to authoritarian rule should explain why repressive regimes often switch SMS networks and restrict Internet access.
- Communication technology ecosystems: Convergence of ICTs is far more powerful than the increasingly ubiquitous mobile phone. When mobile phones and SMS are paired with radio talk show programs, the combination replicates much of the functionalities that characterize the Internet. Once information is broadcase over radio, it becomes public knowledge.
Mobile Tech in Repressive Contexts
I offered to guide a session on Mobile Tech 4 Social Change in Repressive Regimes. The proposal was to identify challenges and opportunities. I stressed the need to look at both tech and tactics since a one-track approach is not full-proof.
Here are the main points I took away from the session:
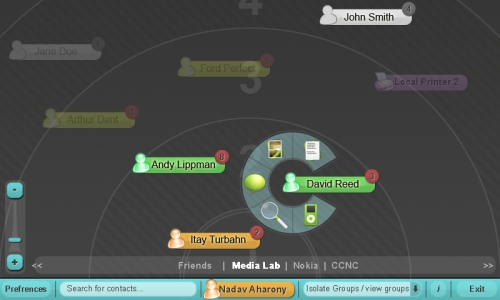
- Ensuring data security in Peer-to-Peer (P2P) meshed mobile communication (see Terranet for example) is very difficult but a 1-hop approach like Comm.unity (screenshot above) is doable and far more secure. The idea is to leverage knowledge, awareness and learning of the user’s social relationships and integrates this information into the communication protocols and network services.” Furthermore, the platform “runs on mobile phones, PDAs, and regular old laptops and PCs, allowing them to easily communicate with each other and build networks of interactions for their users without the need for any centralized servers, coordination, or administration.”
- Steganography is the art and science of writing hidden messages in such a way that no-one apart from the sender and intended recipient even realizes there is a hidden message, a form of security through obscurity. This tactic is one that we should apply more often. Steganography can be applied to images, audio recordings and texts. For example, poems mocking the Burmese junta have appeared in the state-run newspaper using the first word of every sentence in an article.
- Pseudonymity describes a state of disguised identity resulting from the use of a pseudonym. The pseudonym identifies a holder, that is, one or more human beings who possess but do not disclose their true names. Pseudonymity should be more actively used in digital resistance.
Mobile Tech and Communication Security
The second session I participated in was led by Nathanial Freitas. This was an excellent review of the latest tech developments with regards to ensuring that your mobile communications are secure, encrypted, nontraceable, etc. Nathanial used the Android phone as the basis for his presentation. Here are some of the highlights I took away from this informative session:
- Zfone is a new secure VoIP phone software product which lets you make encrypted phone calls over the Internet. Zfone uses a new protocol called ZRTP, which has a better architecture than the other approaches to secure VoIP.
- GetPeek is a new mobile tech that offers unlimited email texting for just $20 a month without the need for a contract. GetPeek will be available in India next week.
- Icognito is an anonymous web browser for the iPhone and iPod.
- Mobile phones that can immediately encrypt, transmit and delete pictures are necessary.
- Browser history on mobile phones should not be deleted as this would be calling attention to oneself. Instead, an alternative browser history should be settable.
- Mobile phones need an actuall off button. Activists always take out the batteries of their phones in order not to have their location traced. Other phones like iPhones do not have a real off button.
- President Obama’s Blackberry has been modified to require fingerprint authenitication.
- The competition between authoritarian control and circumvention by activists is like an arms race, a point I make in my own dissertation research. Andrew Lewman from the Tor Project made a very interesting comment in that regard: “It is very important that this arms race be as slow as possible.” According to Andrew, whatever new technology emerges next is unlikley to be a complete game-changer. Instead of investing considerable time and resources into trying to develop the ultimate tool, he suggests that we take small iterative steps that contribute to momentary advantages in this cyber game of cat-and-mouse.
Mobile Tech, Art and Activism
The final self-organized session I attended addressed the intersection between mobile technology and art for political activism. I’m particulary interested in the subservive art within the context of nonviolent civil resistance.
Here are some of the ideas I took away from this session:
- Stencil art for political activism. “Political stencil art has been significant for centuries as a device for communication and opression. Propoganda was a hallmark of political art in the 20th century in both democratic and communist regimes, at time of war and peace.” See ArtFlux for example.
- Newmindspace is interactive public art, creative cultural interventions and urban bliss dissemination.


Wow what a great roundup! Looking forward to linking to this in a post tomorrow. Thanks!
Thanks Nathaniel! AssetMap looks very interesting!
Great summary, Patrick, thanks. And thanks for participating in the breakout session on how mobile technology might be used to support arts and media activism. To follow up re: stencil activism, I wanted to add Tag You’re Free, the initiative I mentioned to open the discussion. I’m so impressed by this initiative, that Justin Dillon has created in support of his digital engagement platform for the film Call and Response (www.callandresponse.com)– and the fact that it uses stencil art, geotagging, mobile phone photography and performance art is so compelling.
Also, thanks for deepening the discussion on ringtone activism. Here’s the link to the BBC World Service Trust anti-HIV initiative, which is cheeky and effective: http://www.condomcondom.org/
Excellent, thanks for adding these references and thanks for suggesting the breakout session on art mobile activism!
Hi Patrick, great summary.
Another conversation quite interesting was about the work of http://rapidandroid.org
Excellent, many thanks for adding that Rapid Android reference!
Pingback: Zfone - the latest encryption tool for your VOIP client | Aid Worker Daily
Great summary.
Have you seen any research on what changes when people going from simply having access to owning a phone?
Thanks Kevin, haven’t seen any specific research on this topic
Pingback: Heavyset » Mobile Phones and FM Transmitters
Pingback: Midweek roundup… « Radical Instrument
Pingback: Don’t Bury Failures. Share Them
Pingback: Activism or slacktivism: Is the web making it too easy? | memeburn
Pingback: MatchApp: Next Generation Disaster Response App? | iRevolution